Public Key infrastructure is the all in one catch term used for every securing technique that uses key encryption. Today, it is one of the most common modes of encryption that helps users encrypt every form of online data.
PKI certificate allows the people to secure all their online data from being misused. This technology has improved since the past. It is also being adapted in the business industry where companies use this technology to secure their communication.
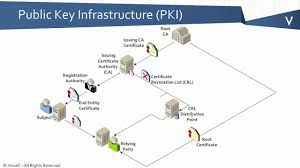
Public Key Infrastructure works on the concept of public cryptographic encryption. The process uses two types of keys: public keys and private keys. These keys are part of the encryption process, but it also helps the users authenticate the identities of the other parties involved in the communication.
Also Read: How to Protect Your Company With a Cybersecurity Service
How Does PKI Work?
To understand the PKI concept, you must have a clear understanding of the keys and the certificates. We all know what keys are. It is a string of keywords and numbers that comes together to form a password.
Let’s understand this by using Caesar cipher’s ancient cryptography method. Caesar Cipher uses a cryptography key to encode its real message. For instance, with the cryptography key of 4, whatever you type in the message will show the 4 letters later in the alphabet. That means, if you type A, the original letter would be E.
The mathematical calculation behind today’s encryption is a lot more complex. In terms of Caesar Cipher, the receiver would know the cryptography key beforehand. However, the users can use keys to secure their communication network in the PKI.
Also Read: The Cybersecurity Risks of Automotive Cloud Computing
What Are PKI Certificates?
You can consider the PKI certificates as passports that let you enter into a secured conversation. These conversations can be used to share all kinds of data. One of the most important pieces of information that the certificate includes is the key.
These keys help the user to get in the network securely. There is also a different mechanism that authenticates every data that is shared in the PKI network.
Here are the following elements that complete the PKI mechanism.
- Certificate authority: It generates a digital certificate that has its public key.
- Register authority: It authenticates the identities of those users who are requesting for digital certificates.
- Certificate database: It stores every document shared in the network.
- Certificate policy: It outlines all the PKI procedures’ privacy and policy and allows outsiders to have a say on its authenticity.
How To Get a PKI Certificate?
From the above description, you can see that trust is the core part of the PKI structure. Applying for the PKI certificate means you are saying to trust you with what you are saying. You even provide documents to support your claim. This is where PKI comes into the frame. It evaluates and validates your every document and provides a certificate that says about your document’s authenticity.
To understand how it works practically, let’s try to understand the most widespread public key infrastructure: TLS/SSL protocol. This protocol secures almost every encrypted HTTP communication.
The SSL and TLS certificate needs to be obtained by the website owner. There are several vendors that have set their shop online selling certificate authority to the websites. However, before you can get that certificate, you need to show them that you are the respective website owner.
What Is PKI Used For?
SSL and TSL might be the PKI’s worldwide implication, but certainly, it is not the only one. PKI application is limitless. You need the right infrastructure to adopt the PKI infrastructure.
Here are the other forms in which you can use PKI infrastructure.
- It provides encryption and recovery keys to the hard drives.
- It secures an internal connection with the database servers.
- Signing in software encryption.
- Secure messaging.
- Email encryption.
- Secure access to the Internet Of Things (IoT).
The Bottom Line
There you have it, Things to know about the PKI system. This might have been a high-level explanation for you, but we have tried our best to give you the best without extending it. If you have any other queries that were not covered in this article, you can drop them in the comment section below. We will get to you with an answer as soon as possible.
Also Read: How to Start Your Career in Cyber Security